SecuX Author : K. Yang, CISO & CIO, SecuX Technology Inc. 安瀚科技股份有限公司
The global blockchain ecosystem has undergone significant growth and evolution over the past decade. It encompasses a wide range of businesses and enterprises, including information system integrators, fintech integrators, financial holdings, banks, life insurance companies, and other fintech industries. The blockchain ecosystem has also been integrated into several sectors, such as cryptocurrency exchanges, both domestic and foreign, cryptocurrency software, hardware wallets, healthcare, cashless payments, digital asset integrators, supply chains, logistics companies, business service providers, e-commerce, media services, and many more.
In terms of security, common forms of cyberattacks are analyzed and taken into consideration within the blockchain ecosystem. As the use of cryptocurrency and digital assets continues to grow, it’s important for individuals to take proper steps to ensure the safety of their assets. One of the recommended solutions is the use of a hardware wallet, also known as a cold wallet or crypto wallet, which offers enhanced security by holding private keys offline and offering protection against both physical and online attacks. Overall, the integration of blockchain technology has expanded and diversified, creating new opportunities and innovations in various industries.
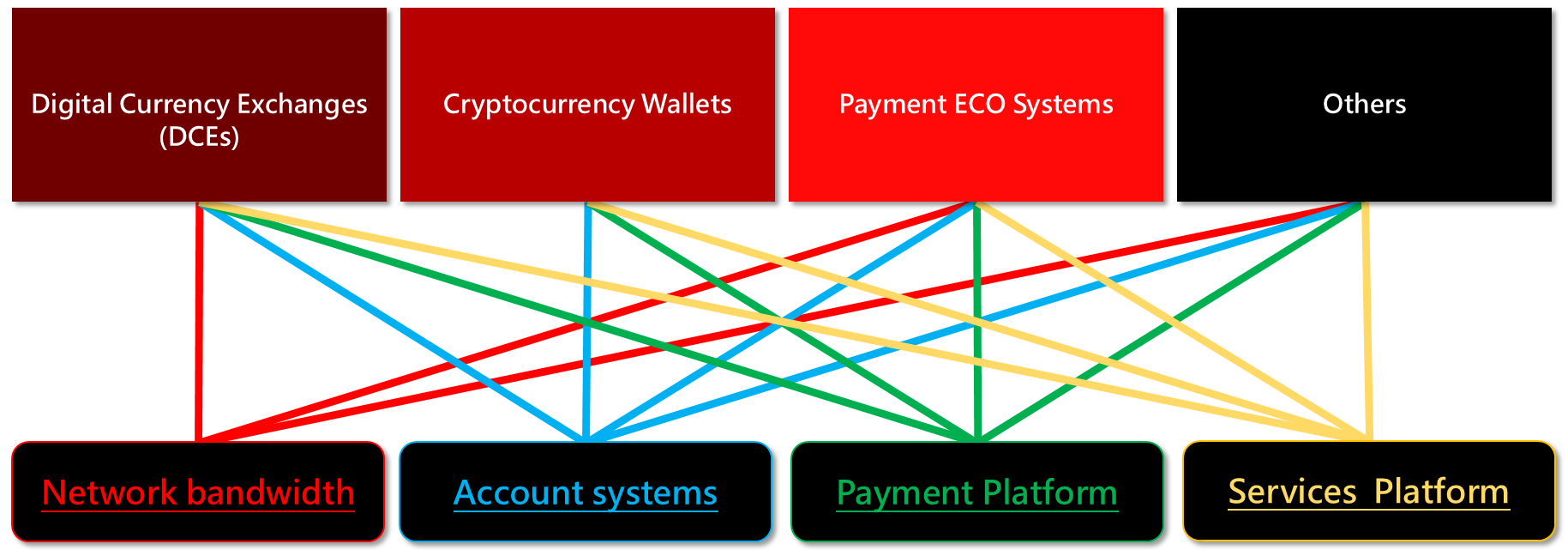
Figure 1 lists digital currency exchanges (DCE), different types of cryptocurrency wallets, payment ecosystems, and other e-commerce service software, programs, or platforms offered by players in blockchain-related service industries.
Among the common types of cyberattacks, damage or disruption to the network bandwidth (in the lower left corner of the figure) includes DDoS (Distributed Denial-of-Service) attacks which aim to exhaust the resources of the targeted network or system to crash its services. Eg. Affecting normal transactions or causing currency fluctuations.
The second type of attack, is one targetting account systems (in the lower left corner of the figure) including phishing, user-end cracking using reverse engineering, installing backdoor or Trojan viruses, scams and frauds, wiretapping, traffic analysis and masquerading, message modification, man-in-the-middle attacks, and so on. E.g. Stealing accounts, modifying addresses, and transferring ownership in digital assets.
Attacks to payment and relevant services platforms include exploiting vulnerabilities, loopholes, zero-day threats in web apps codes, using hacking software or self-developed software to intrude the information system and obtain the administrative permission to unlawfully use the system to gain legitimate access and authorization; ultimately stealing users’ important data or information, or transferring users’ digital asset.
The following is an excerpt featuring major security issues concerning blockchain (2011~2019), including brief descriptions on the types of attack and methods of intrusion:

In summary of previous cyber attacks, the major methods of attack used by hackers include traditional threats such as intruding an ordinary server, cracking or stealing the administrator’s password without the admin’s knowing; or infecting a user’s computer with a backdoor or Trojan virus in order to stealing key and verifications of software wallets, thereby gaining permission and transfering the user’s digital assests.
In a cryptocurrency exchange, hackers take advantage of the loopholes in the codes of the exchange’s website or invade the system by exploiting zero-day vulnerabilities (that is unknown) to transfer digital currency. Additionaly, they could make use of system weaknesses, or use advanced persistent threats (APT) to discover zero-day vulnerabilities. This allows the invaders to take a detour and bypass the multiple verifications and security control management systems of the internal server, causing abnormal transactions or currency fluctuations.
Other threats include hackers gaining a user’s account through a phishing website and stealing their assets; or installing a virus on the system admin’s computer to acquire the account and passwords required to attack local servers on blockchain nodes; or getting access to exchange transaction servers to gain system permission; obtain great number of user accounts, keys, and confidential and sensitive information and transfer large sums of digital currency.
In May 2019, an exchange system was attacked by attackers using large-scale and long-term attacks. This resulted in a great number of API (application programming interface) keys and Google two-factor authentication (2FA) codes being stolen. Additionally, loopholes in the online top-up function of the exchange were found, resulting in great losses. Last November, the free mining incident occurred. The hacker exploited the loopholes of the system to maliciously mine EIDOS and cause CPU exhaustion. In the same month, a South Korean cryptocurrency exchange – Upbit was attacked and lost 342,000 ETH (Ethereum).
In January 2020, a US exchange Poloniex was reported to have system errors. All transaction records within a period of 12 minutes were reversed, but details of this event were not disclosed.
To successfully invade and attack an information system of a certain scale, such as a large digital currency exchange, a bank of a financial holdings company, or a payment ecosystem based on different large frameworks, preparations aren’t compleeted overnight. So how do malicious attackers or invaders successfully attack or gain access to the systems?
In fact, this way of attack can be defined as a specific, multistage, and long-term and continuous attack. Attackers conduct a strategic analysis, evaluation, planning for the target and then launch a series of organized invasions and attacks through formal channels. They are known as APT (Advanced Persistent Threat) attacks in the field of cybersecurity.
Since APT attacks are highly-specific, multistage, long-term, and “continuous” attacks, the attacker adopts a set of scripts of system penetration or infiltration methods. If this does not work, then the attacker will come up with another set of methods until he/she is successful. Please note that it is “a set” instead of “a type”. DDN plays an important role here because all the security controls and checkpoints will cost the attacker more time and space, therefore requiring further assessment, consideration, as well as a decision on the amout of resources to be invested.
In my previous article The Edge Computing endpoints and Defense-in-Depth Network security issues and recent developments, the design concept of the DDN was mentioned, which is believed to be the basic security defensive mechanism of an information infrastructure. However, if you want to reduce or counter the security risks caused by APTs, newer and enhanced security mechanisms aside from DDN will have to be implemented. There are many discussions about the APT, but every one of them has its own reasoning. The following is my definitions and explanation of the APT. The steps of the APT attacks are as follows:
1. Planning for the Target: The attacker evaluates and confirms (1) the attack target, (2) difficulty of attack, (3) attacking the targeted information system, (4) the defensive mechanisms, systems, and information security staff, (5) scheduled dates and times, and (6) costs required. After confirming these, thorough research and detailed analysis will be conducted. The APT will work as a group cooperating to finish the planning and move on to the next stage, starting a series of attacks like an ongoing marathon.
2. Intruding or Penetrating the Target: In the first stage, thorough research on the target is conducted and analyzed over a long period of time. Multiple scripts and methods of attacks have been defined. Then, a series of attacks (detection, testing, and invasion) are carried out. Finally, the attacker successfully intrudes the targeted system and completes all necessary tasks in this stage. Note: Methods of attacks include social engineering, internet phishing, brute-force attacks. The attacks are flexible, complicated, and consist of various methods, tools and ways of invasion. (Details are not discussed here.)
3. Taking Control and Obtaining Valuable Information: When an attacker enters the targeted information system and environment, the attacker starts one of the most important tasks — getting a higher system permission. When attacker obtains a higher system permission, they can take control of the system and start stealing valuable information and data.
4. Installing Programs in the Targeted Information System, as follows:
(1) The attacker starts to install multiple self-developed software programs using zero-day attacks. Theese self-developed programs have no signature for an anti-virus database to cross-reference because it is not an existing virus pattern (VP), so no virus scan engines can detect them, and they may be able to avoid intrusion detection systems (IDS), intrusion prevention systems (IPS), as well as an intrusion response systems (IRS).
(2) The intruder fully understands the program and its hacking. It adopts a slow-rate attacks and avoids any signature matching mechanisms to prevent triggering an alert from the detection or response systems. As it excludes all pattern matching algorithms in intrusion detection, the defensive security system you use probably cannot detect or discover it as if it is invisible. (Note: Patterns of attacks and signatures of codes are not foreseeable and cannot be defined beforehand. The existing IPSs and IDSs all employ default responses or protection measures to stop known methods of attacks.)
(3) These programs may be installed in your system for a long period of time. In fact, they could be different kinds of self-developed Trojans and backdoors, botnets or zombies controlled by a bot herder. One common way is to compile different types of self-developed rootkits into your kernel. It is similar to using a honeypot, but the target is different, and it uses A-B-T.
5. Intruders Hiding Themselves and Removing Their Traces: An intruder remains undiscovered and removes their traces when entering and leaving an information system.
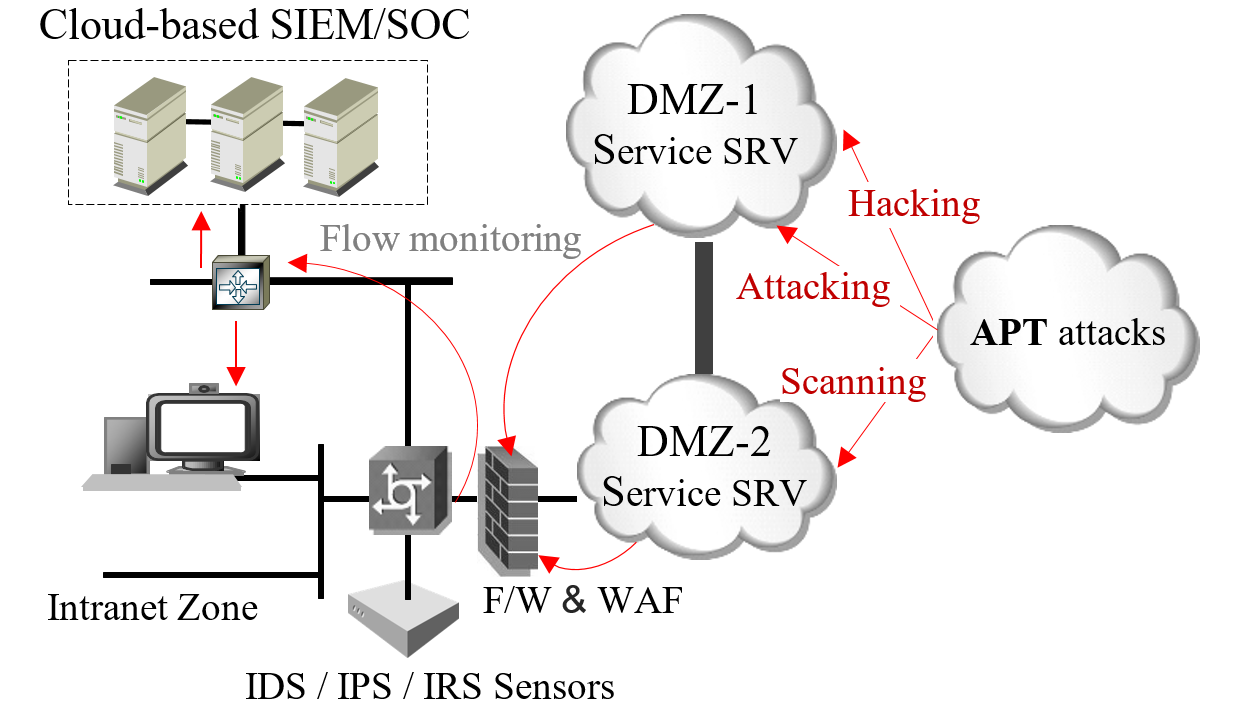
The blockchain ecosystem is one of the favorite ecosystems for attackers. How do we prevent APT attacks? What are the security protection strategies?
In addition to the basic defense-in-depth network design, the followings have to be reviewed and evaluated a second time:
1. Access permission of all system admins have to reviewed, you have to make sure admins understand the security issues and potential risks of APTs, which is a necessary concept and prior knowledge for system admins.
2. All information systems, system admins, external users linking to your system/network and having abnormal network traffic have to monitored so that all abnormal system behaviors are under control.
3. A messaging feedback mechanism can instantly notify the cybersecurity staff and take intrusion response (IR) measures in the shortest time possible or take emergency measures to raise the security defense level.
4. A review and inventory of data and information needed for better protection has to be done. In other words, classification and management of information assets have to completed in advance to make sure which type and level of security risks the information belongs to and what information is the one that attackers want most. Any type of information can become targets of attackers. By doing so, it is clear which part needs further protection.
In addition to the three major keypoints mentined above, having a basic understanding of information security and protection (for example, social engineering, internet phishing, regular system updates, checks, software patching, stronger password managers in certain systems, vulnerability analysis and assessment, and independent system software testing), deploying a defense-in-depth mechanism, and setting up a security information and event management system (SIEM) center are also necessary.
Moreover, larger organizations, network operation centers (NOC), and security operation centers (SOC) are capable of more timely response to security issues and track potential security threats by implementing comprehensive security monitoring and management mechanisms. Furthermore, regular drills (such as business continuity management, business continuity plans, disaster recovery plans) in response to all kinds of security issues are included in the scope of ISO/IEC.
Keeping oneself up to date can effectively alleviate existing problems or predict potential APTs. When an attacker intrudes or is in the stages of preparation, the security information management system center with a certain level of a security management mechanisms rapidly respond to abnormal internet behaviors and traces. The attacker might carry out a test, detection, collection of our system information. It is in times like these that we can react or act promptly, therefore minimizing the potential damage and system securitys.