SecuX Author : Sam Lin , VP @ SecuX Technology Inc. 安瀚科技股份有限公司
Cryptocurrency, also known as virtual currency, was first introduced in 2008 through an article written by Satoshi Nakamoto entitled “Bitcoin: A Peer-to-Peer Electronic Cash System.” The article described a new electronic currency called “Bitcoin” and its underlying algorithm. On January 3, 2009, Satoshi successfully mined the first batch of 50 Bitcoins, marking the beginning of the Bitcoin financial system and the new era of cryptocurrency. Today, there are over a hundred types of cryptocurrency available, with thousands of tokens in total when taking into account ERC-20.
When it comes to safeguarding these valuable assets, it is crucial to choose the right wallet to store them. That is where hardware wallet like SecuX and cold wallet come into play. These wallets provide a high level of security for your cryptocurrencies and give you peace of mind that your assets are protected. In addition, SecuX’s crypto wallet support cross-border and peer-to-peer transactions, making it convenient for foreign workers and cryptocurrency investors to manage their assets from home. SecuX also offers a world-first crypto payment solution, making it easier and more secure to process payments in physical retail businesses with contactless technology.
Thus, the well-known blockchain was born with the Bitcoin marking an epoch-making milestone.
1. Decentralization: In order to emphasize the sharable feature of the blockchain, the user doesn’t need to rely on the additional regulatory institutions or hardware facilities, so that the centralized mechanism is not required as well. Therefore, the data on each blockchain is stored on different nodes. Accounting and storage are both distributed. Every node has to self-verify, deliver, and manage. Decentralization is the most prominent core feature of the blockchain.
2. Intamperable: After each piece of data on the blockchain is imported, it cannot be modified. Once the data is validated, it is permanently imported on the block. The technology is to ensure the data to be intamperable through the Hash Algorithm. Such function can be easily validated but hard to decipher. It is hard to extrapolate the original value, so the data is intamperable.
3. Anonymity: Since the information on the blockchain doesn’t have to be publicly validated, the exchange of information between two parties can be completed anonymously.
4. Consensus Mechanism: The Proof of Work (POW) System is used to incentivize miners to maintain the system operation.
5. The reward is halved every 4 years in order to control the total amount of the Bitcoin.
6. The source code is open, so everyone can take part in the security validation process.
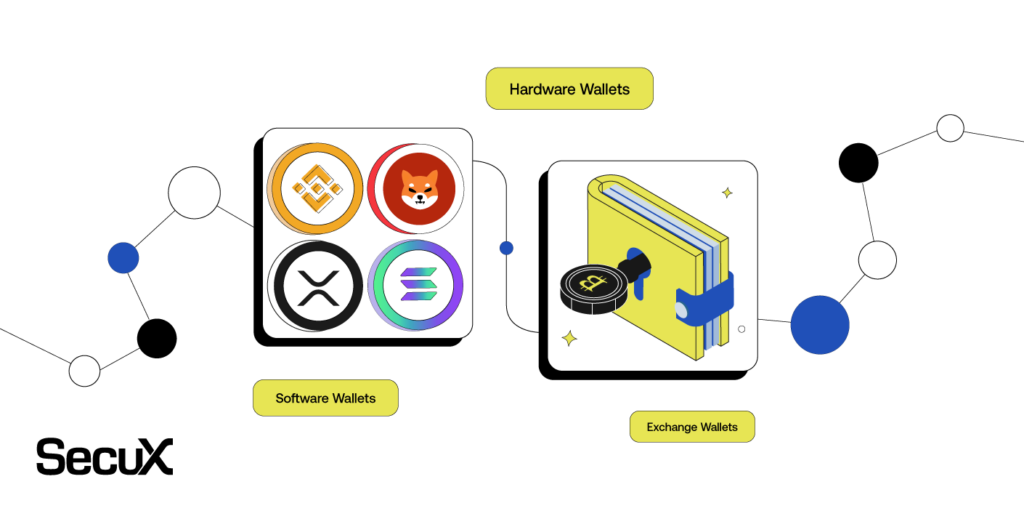
The cryptocurrency can be stored either in the custody account or kept individually. The custody account is to keep the individual cryptocurrency in the exchange, so the cryptocurrency trading is processed through the exchange which can deal with the trading of different types of cryptocurrencies as well as the exchange from fiat money to cryptocurrency. The individual storage depends on the cryptocurrency wallet to trade. When the individual intends to receive the cryptocurrency, the wallet will generate the address for the sender. When the individual intends to send the cryptocurrency, the wallet will generate the data with a private key signature and send it to the blockchain. The most critical aspect of the cryptocurrency asset is the private key storage. If the private key is disclosed, the entire cryptocurrency asset will be lost. Therefore, how to strictly secure the private key is the vital issue of the cryptocurrency.
The cryptocurrency wallet can be divided into the software wallet and hardware wallet. The software wallet normally stores the private key on the computer or cell phone. On the other hand, the hardware wallet is an independent device that can be used to store the private key. Owing to constant Internet connection, the software wallet is easily hacked and the private key within is stolen quite often. Nevertheless, the hardware wallet only connects to the Internet while trading, and an independent device is hard to be hacked, so the private key will not be stolen during the Internet connection. The private key in the hardware wallet can be divided into the ordinary memory and the memory with the high-level security certification (CCEAL5+). Despite the fact that the private key in the hardware wallet will not be stolen during connection, the private key stored in the ordinary memory can still be detected when the device is lost or stolen. The private key stored in the memory with the high-level security certification is undetectable, so it ensures better security.
In addition, there is another type of special wallet called “paper wallet”. Every paper wallet stores a fixed amount of cryptocurrency, for example, 0.01 BTC or 0.001 BTC. The private key is printed on the paper wallet according to the BIP38 standard. Only with a passphrase, the private key can be decrypted, and the cryptocurrency can be used. Additionally, the software is also required to transfer the cryptocurrency. The wallet is just like cash. In other words, the individual can directly buy cryptocurrency in cash and transfer it to other wallets.
There are many types of hardware wallets, including the card type, non-card type, small screen, large screen, button type, touchscreen, some included battery and some not, etc. The card type hardware wallet is highly portable but provides limited interface and functions. The hardware wallet with a small screen can only display limited information and the operation is quite troublesome. The hardware wallet with a large screen can display more information and the operation is much easier with the touchscreen, coupled with some securer validation mechanisms.
The hardware wallet is only connected to the Internet while trading, or it remains offline. While trading, the hardware wallet must be connected to the host device to link it to the Internet. The host device may be a computer, laptop, cell phone, etc., and the host system can be Windows, Mac OS, Linux, Android, iOS, etc. The interface connected to the host device includes the USB, Bluetooth, NFC, QR Code, SD Card, etc. The USB is a standard interface on the computer with high speed, easy connection and the charging function. The Bluetooth is commonly used to connect to the hardware wallet with the cell phone. Some laptops can use the Bluetooth to connect to the hardware wallet. Although the signal may be detected by the nearby device, the problem will be solved if the data transmission is encrypted. Even though the data can be read by the nearby device, the data still remains secure and incorruptible. However, the asset amount will be leaked if the data is cracked. Some hardware wallets use the QR Code to transmit the data without “Man-in-the-middle attack” (MITM). However, scanning code repeatedly is extremely troublesome while transmitting the data. Some hardware wallets use the NFC interface to connect to the cell phone for data transmission. If the data transmission is conducted at a close distance, it will not be detected and can prevent the MITM attack. However, if the hardware wallet and the cell phone both require the information input at the same time, the operation will become extremely troublesome.
The cryptocurrency asset is stored on the blockchain. The private key is required if the individual wants to use the asset. Therefore, the private key storage is extremely important. Bitcoin has resolved the problem of interoperability by proposing the standard of BIP-39, BIP-32, and BIP-44. To date, most of the cryptocurrencies have adopted these standards. As long as the cryptocurrency wallet meets the standards, the asset can be immediately transferred to other wallets that meet the standards when the hardware wallet is lost or stolen. The BIP-39 standard private key can generate a 12/18/24 word phrase. Take a 24-word phrase for example, the individual has to remember the 24-word phrase to recover the private key in any wallets. When the user wants to input the 24-word phrase for recovery, the hardware wallet with a large touchscreen will be convenient to operate.